Continuous Integration and Continuous Delivery (CI/CD) streamline the software development lifecycle. This article explores how CI/CD automates code building, testing, and deployment processes. Discover how CI/CD can accelerate software delivery, improve code quality, and empower your development teams to deliver innovative solutions faster. Understanding Continuous Integration (CI) Continuous Integration (CI) is a cornerstone of modern software development practices. It revolves
IT governance establishes a framework for aligning IT strategy with business objectives while ensuring regulatory compliance and managing risks. This article explores the core principles of IT governance, including IT policy development, resource management, and IT risk management strategies. Discover how effective IT governance can empower your organization to leverage technology effectively and mitigate IT-related risks. Understanding Risk Management in
Your network is the backbone of your IT infrastructure. Network monitoring tools provide continuous visibility into network performance and health. This article explores different network monitoring tools and their capabilities. Learn how to identify network bottlenecks, troubleshoot issues proactively, and ensure optimal network performance for your users and applications. Importance of Network Performance In today’s interconnected world, where businesses rely
Email remains a prime target for cyberattacks. Phishing scams and malware attachments can wreak havoc on your organization. This article explores essential email security measures, including user education, spam filtering, and robust email security solutions. Discover how to fortify your email defenses and protect your users from falling victim to email-borne threats. Understanding Phishing Attacks Phishing attacks are deceptive tactics
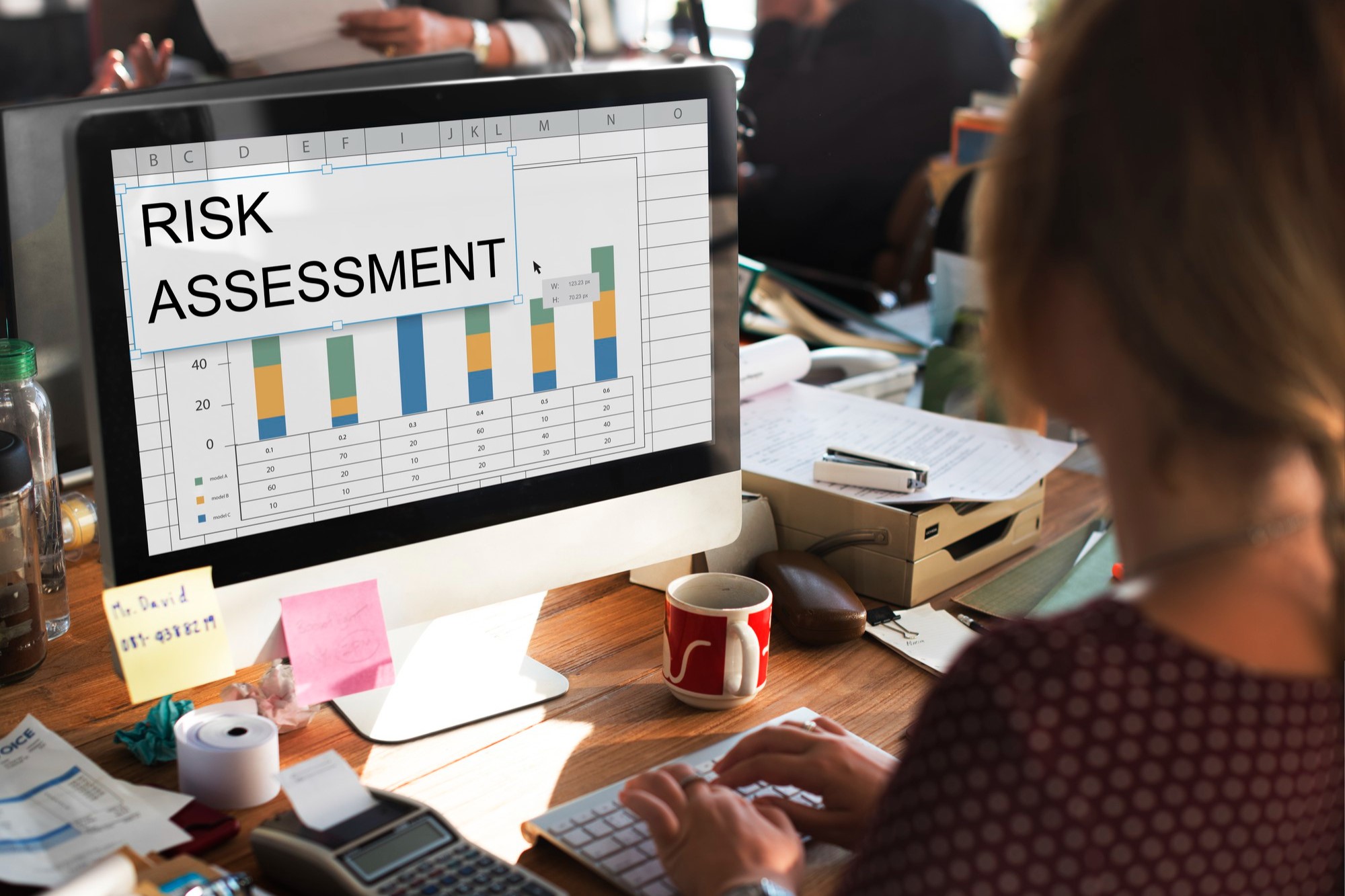
Proactive risk management is essential for any organization. An IT risk assessment helps identify potential threats and vulnerabilities in your IT infrastructure. This article explores the IT risk assessment process, outlining methodologies for evaluating risks and prioritizing mitigation strategies. Learn how to safeguard your organization from cyberattacks, data breaches, and other IT disruptions. Importance of IT Risk Assessment In today’s
Containerization is revolutionizing application deployment. Imagine self-contained packages that run consistently across any environment. This article explores the benefits of containerization, including faster deployments, improved scalability, and simplified application management. Discover how containerization can streamline your software development lifecycle. What is Containerization? Containerization is a modern software development approach that involves encapsulating an application and its dependencies into a self-contained